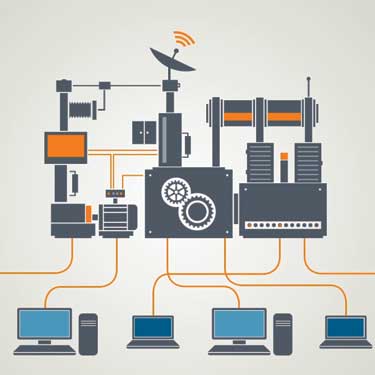
PLC & Distributed I/O Products
Every application has unique requirements regarding system performance and complexity. With PLC & Distributed I/O solutions from Siemens, Kepware and Weidmueller PCC offers our customers an extensive range of controller and I/O options from simple stand-alone applications to advanced distributed, decentralized and fail-safe architectures. Options available include programmable relays, micro PLCs, compact PLCs, PC-based control, PLC/HMI, fail-safe PLC & I/O, OPC servers, high density modular I/O, slice I/O, IP65/67 block/modular I/O, and intrinsically safe I/O.
Featured PLC & Distributed I/O Products
PLC & Distributed I/O News
Video: What’s new for SIEMENS LOGO! 8
Siemens TIA Portal Tutorial S7-1200
Be Not Afraid — The Time has come to Trust Safety Rated PLCs
By Tim Parmer, Siemens Energy and Automation Safety PLCs combine the functionality of a control system with a safety system in one controller platform, allowing manufacturers to greatly reduce machine life cycle costs. An advantage of...
White Paper: Best Practices for Automating Security
Historically, automation systems have relied on “security through obscurity“ to avoid computer attacks. Those days are gone. While the number of actual attacks on automation systems has been small, the tools needed to conduct these attacks...